There is no evidence of a Twitter data breach
In June 2016 it was reported that 32,888,300 login details of Twitter users had been put up for sale on the Dark Web. A user going by the alias Tessa88@exploit.im was asking for 10 bitcoins (worth around £4060.20 then) from anyone that wanted a copy of the list. Twitter however, was confident that this was not a breach of its network.
It was believed that the details may have been gathered from combining information from other recent website breaches, malware on victim machines that are stealing passwords for all sites, or a combination of both. Twitter had cross-checked data with their own records and Twitter accounts identified for extra protection had been locked and required a password reset by the account owner.
LeakedSource, a site that kept a database of leaked login credentials, added a copy of the data to their searchable repository of leaked data. Credentials on the list had been verified as real and valid and LeakedSource used the following explanation as proof this was not a Twitter data breach.
The join dates of some users with uncrackable (yet plaintext) passwords were recent. There is no way that Twitter stores passwords in plaintext in 2014 for example.
There was a very significant amount of users with the password “<blank>” and “null”. Some browsers store passwords as “<blank>” if you don’t enter a password when you save your credentials.
The top email domains don’t match up to a full database leak, more likely the malware was spread to Russians.
Password concerns
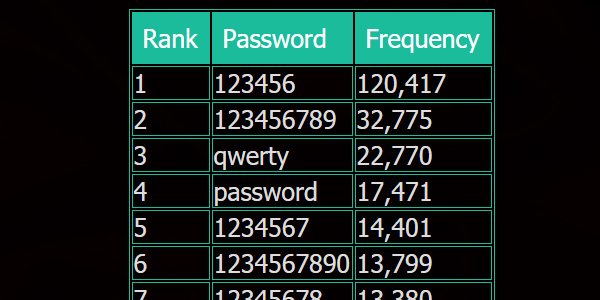
LeakedSource also listed some of the passwords Twitter users used and it shows that there are a lot of people who are not following good password practices. You can read an earlier post of mine regarding password security and if you are using simple passwords and/or using them on multiple sites, change your habits now.
Malware concerns
There is still a large concern of malware harvesting credentials, not just for Twitter but for any website that your browser may have saved passwords for. Check your computer regularly for viruses and malware, if you don’t feel confident in doing this, take your computer to a local computer repair company and ask them to check for you.

